CerberAuth
Authentication solutions and security automation for safer, faster, and smarter development.
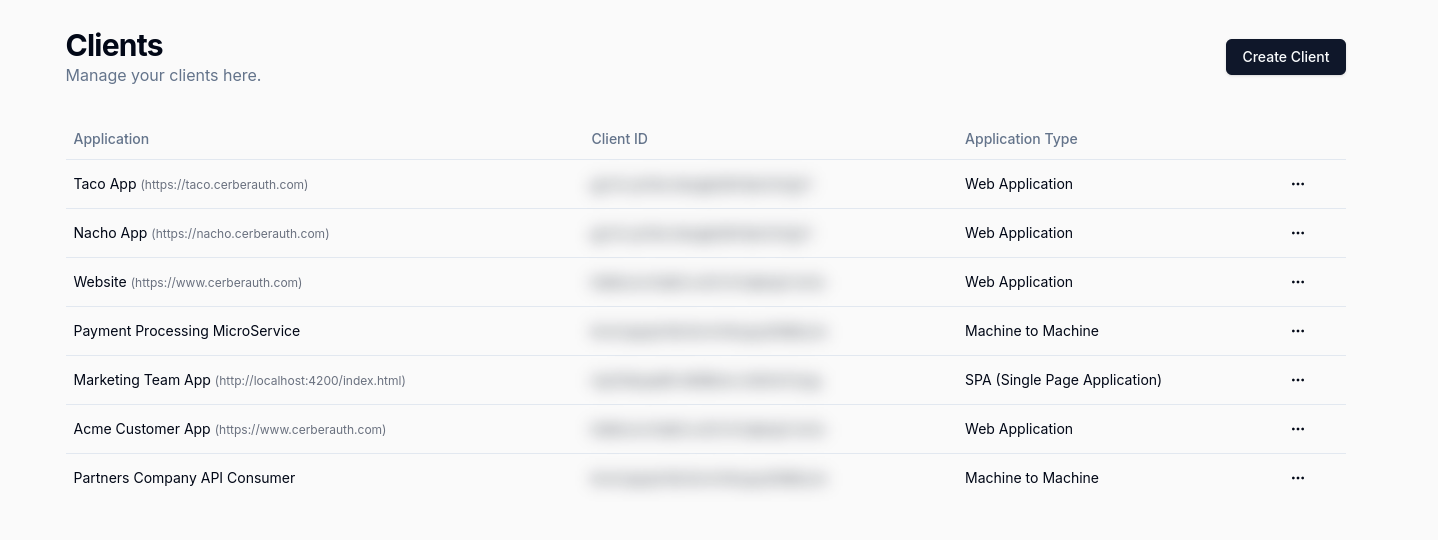
The Ecosystem
Our ecosystem is designed to help you build secure applications faster with a suite of services covering OpenID Connect clients onboarding, client integration testing, and API Security automation.
VulnAPI
An API Security Vulnerability Scanner designed to help you secure your APIs.

Nacho
Designed to be used by developers and non-developers alike, and it is meant to be a simple and easy-to-use tool to help you create OAuth 2.0 clients for your applications.
Taco
Validate OpenID Connect client creation, control API access, and ease clients management.
Ready to join this
Community?
Join our vibrant Discord community! Connect, share, and grow with like-minded enthusiasts. Click to dive in! 🚀


