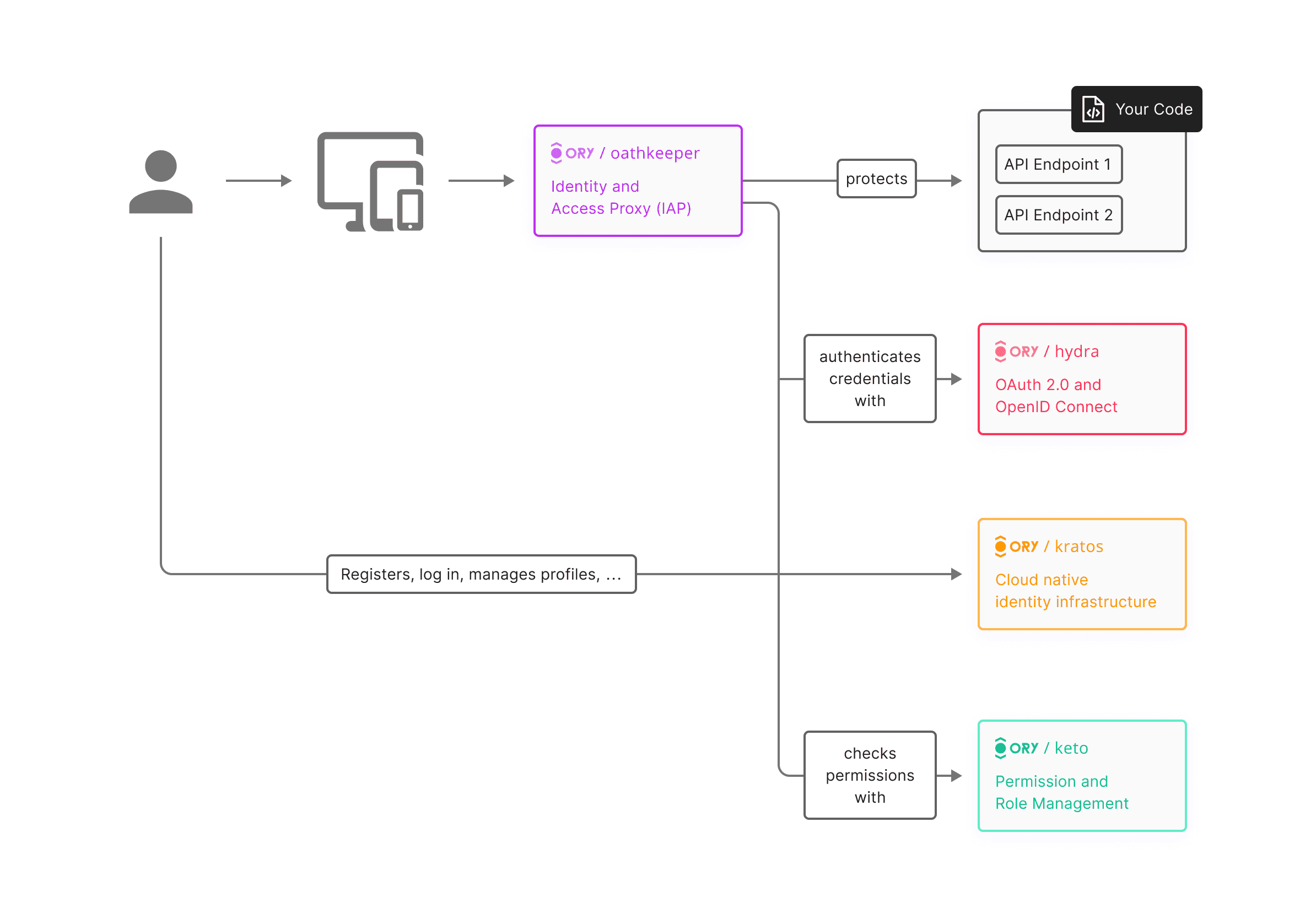
What is the difference between Authentication, Application authorization and Access Control?

Understanding the nuances between authentication, authorization, and fine-grained authorization is crucial. These concepts form the backbone of identity and access management (IAM) systems, laying the groundwork for securing digital assets and ensuring that users have the appropriate levels of access.
Yet, the terms are often used interchangeably or misunderstood, leading to confusion among users and organizations. In this article, we'll delve into the distinctions between authentication, authorization, and fine-grained authorization, clarifying their roles and importance in safeguarding sensitive information and resources.
Authentication: Verifying Identity
Authentication is the process of verifying the identity of a user or system entity attempting to access resources or services. It ensures that the individual or entity claiming a particular identity is indeed who they pretend to be.
Authentication serves as the first line of defense in securing digital assets and resources. By confirming the legitimacy of users, systems, or devices, authentication helps prevent unauthorized access, data breaches, and other security threats. Without robust authentication mechanisms in place, organizations risk exposing confidential information, compromising data integrity, and damaging their reputation.
Authentication Factors
Authentication relies on various factors to validate an individual's identity. These factors can be categorized into three main types:
- Knowledge-based factors: These factors require users to prove their identity through something they know, such as a password, PIN, or passphrase.
- Possession-based factors: These factors involve something the user possesses, such as a physical token, smart card, or mobile device, which generates one-time passwords or authentication codes.
- Inherence-based factors: Also known as biometric factors, these rely on unique physical or behavioral characteristics of the user, such as fingerprints, iris scans, facial recognition, or voice patterns.
Application Authorization
Application authorization, also referred to as applicative authorization, pertains specifically to the process of granting permissions and privileges to individual applications or software components within a system.
Unlike user-level authorization, which focuses on controlling access based on user identities, applicative authorization governs the actions and behaviors of specific applications within an environment.
Importance of Application Authorization
Application authorization governs the extent to which a third-party application can access certain information or perform actions on behalf of a user. While an application may successfully authenticate a user, it does not automatically grant the application unrestricted access to all of the user's data and resources. Instead, application authorization determines the specific permissions and privileges granted to the application, ensuring that it operates within predefined boundaries and adheres to security policies.
In scenarios where a user grants permission to a third-party application to access their data or perform actions on their behalf, application authorization mechanisms play a crucial role in enforcing these permissions. For example, in OAuth-based authentication flows commonly used in modern applications, users authorize third-party applications to access their data stored in other services (such as social media platforms or cloud storage) through the issuance of access tokens. However, the level of access granted to these applications is governed by the authorization server, which enforces the scopes or permissions specified by the user during the authorization process.
Without effective application authorization controls in place, third-party applications could potentially exploit their access privileges to gain unauthorized access to sensitive information or perform malicious actions on behalf of users. By implementing robust authorization mechanisms, organizations can ensure that third-party applications operate within the confines of their intended functionality and adhere to the principle of least privilege, thereby mitigating the risk of data breaches, privacy violations, and other security threats.
Access Control (Fine-Grained Authorization): Granular Identity Permissions
Fine-grained authorization, also known as granular identity permissions, represents a sophisticated approach to access control that enables organizations to define highly specific permissions and privileges for individual users or entities within a system.
Fine-grained authorization addresses the limitations of traditional access control models by offering a more nuanced and flexible approach to managing access permissions. By granting or restricting access at a granular level, organizations can tailor permissions to align with the specific requirements and responsibilities of individual users or system components, thereby enhancing security, compliance, and operational efficiency.
Key Aspects of Fine-Grained Authorization
- Attribute-Based Access Control (ABAC): Fine-grained authorization often leverages attribute-based access control (ABAC) frameworks, which evaluate access decisions based on a wide range of attributes associated with users, resources, and contextual factors. These attributes may include user roles, job functions, organizational affiliations, time of access, location, device characteristics, and other relevant parameters.
- Dynamic Access Policies: Fine-grained authorization enables the implementation of dynamic access policies that adapt to changing circumstances or user contexts in real-time. These policies may incorporate dynamic attributes such as user attributes, environmental conditions, or risk factors to make access control decisions dynamically, ensuring that access permissions remain appropriate and aligned with evolving requirements.
- Resource-Level Permissions: Fine-grained authorization extends access control down to the level of individual resources or data elements within an application or system. This granular approach allows organizations to define precise permissions for accessing, modifying, or deleting specific data objects or functionalities, granting users only the permissions necessary to perform their tasks while minimizing the risk of unauthorized access or data leakage.
- Role-Based Permission Inheritance: Fine-grained authorization frameworks may also support role-based permission inheritance, where users inherit permissions dynamically based on their roles, group memberships, or organizational hierarchies. However, unlike traditional role-based access control (RBAC) models, fine-grained authorization allows for the fine-tuning of permissions at the individual level, overriding or augmenting inherited permissions as needed.
Several Solutions to Specific Needs
When it comes to implementing fine-grained permissions, it's essential to recognize that various solutions exist, each catering to different needs and use cases.
The choice of solution depends on factors such as the complexity of the access control requirements, the scale of the system, and the level of flexibility and control desired by the organization.
Consideration of Different Solutions:
- Role or group claim in JWTs for Role-Based Authorization:
- Advantages: It leverages existing OAuth infrastructure and standards, allowing organizations to extend their OAuth implementations to incorporate fine-grained permissions easily. It is scalable since the role verification can be distributed across the different components.
- Limitations: While effective for role-based authorization, this approach may lack the sophistication and scalability required for managing complex access control policies in large-scale distributed systems.
- Zanzibar for Permission Management:
- Advantages: It offers a centralized, distributed permission management system that supports hierarchical organization of permissions and efficient querying and enforcement mechanisms.
- Limitations: Implementing Zanzibar may require significant upfront investment in infrastructure and development effort, making it more suitable for organizations with complex access control requirements and robust technical capabilities.
By embracing fine-grained authorization mechanisms, organizations can strengthen their overall security posture, achieve greater regulatory compliance, and empower users with the appropriate level of access to resources, ultimately supporting business agility and innovation while mitigating security risks.