Users accounts for your SaaS - A Journey with Ory Solutions

Welcome to this blog post series dedicated to security within the Software as a Service (SaaS) landscape.
In the upcoming segments of our SaaS security blog series, we will cover critical topics aimed at enhancing your understanding of modern security frameworks. We'll explore Customer Identity and Access Management (CIAM) strategies, examine the details of OAuth2 and OpenID Connect protocols, discuss API security measures, and investigate the global authorization system landscape, with a specific focus on the Zanzibar system.
Each topic is a crucial component of the broader security landscape, and collectively, we aim to provide you with a comprehensive view of how these elements work together to strengthen your SaaS environment against evolving threats. Stay tuned for insights, practical approaches, and strategies to reinforce your organization's security posture in a dynamic digital landscape.
We're bringing a nifty TODO app along for the ride as our guinea pig, to show you real-world scenarios.
Introducing Ory
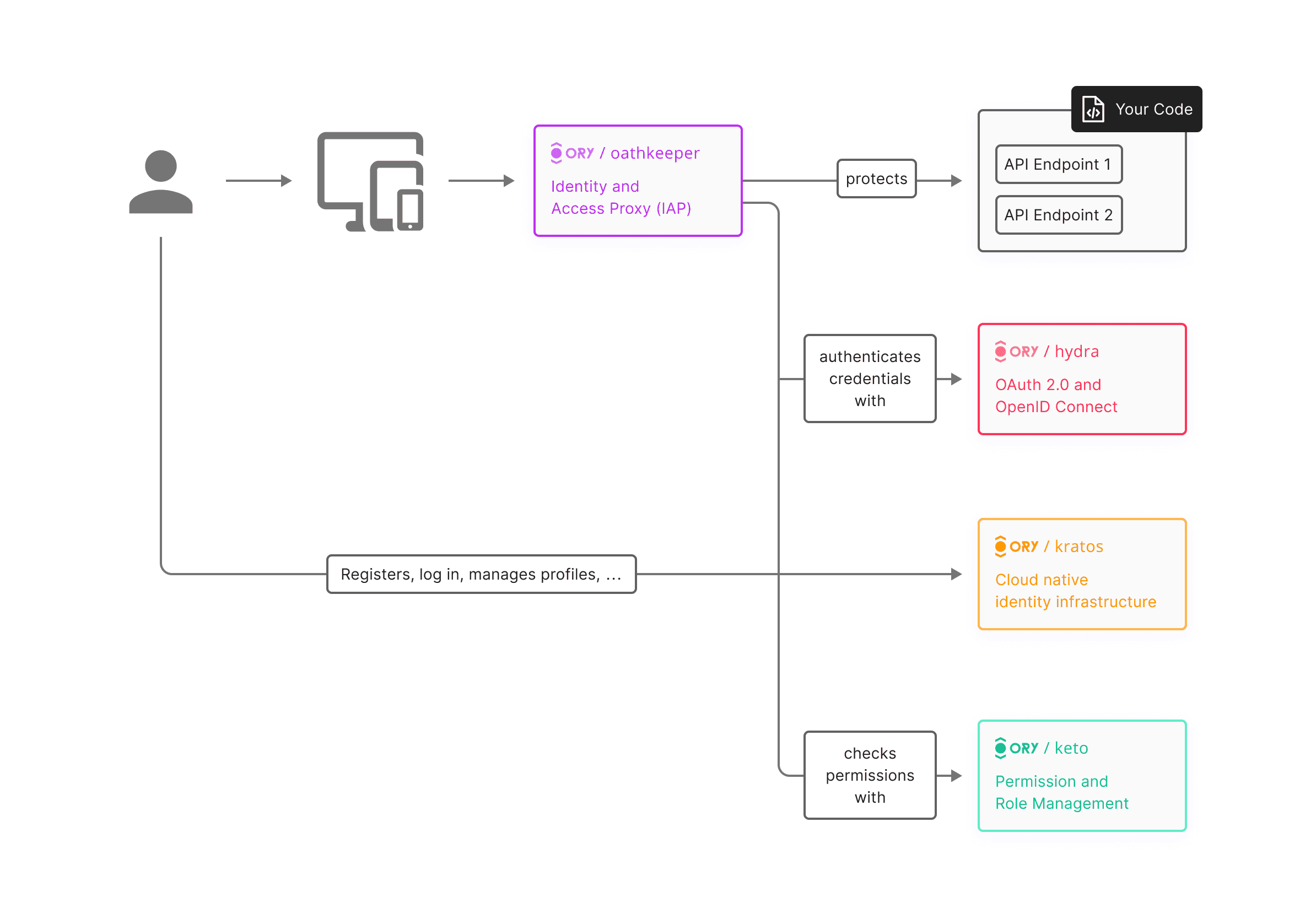
Let's take a moment to meet the rockstars of our journey – the incredible suite of solutions developed by Ory.
Now, before we dive into the details, here's the coolest part – all of Ory's products are open source giving you the freedom to read the code, explore, customize, and contribute to the very core of the security solutions. The transparency and collaboration of open source not only enhance your control but also foster a global community of security advocates.
Throughout this blog series on SaaS security, we'll be leveraging cutting-edge solutions from Ory to address key facets of identity and access management. Ory Kratos will take center stage, providing insights into effective Customer Identity and Access Management (CIAM) strategies. For the intricacies of OAuth2 and OpenID Connect protocols, we'll turn to Ory Hydra, exploring its functionalities for secure and seamless authentication. Dive into the world of API security with Ory Oathkeeper, uncovering how it ensures robust protection for your application interfaces. Additionally, we'll shine a spotlight on Ory Keto as we unravel the complexities of the Zanzibar global authorization system, demonstrating how it plays a pivotal role in managing permissions efficiently. Join us on this journey as we harness the power of Ory's solutions to fortify your SaaS security framework.
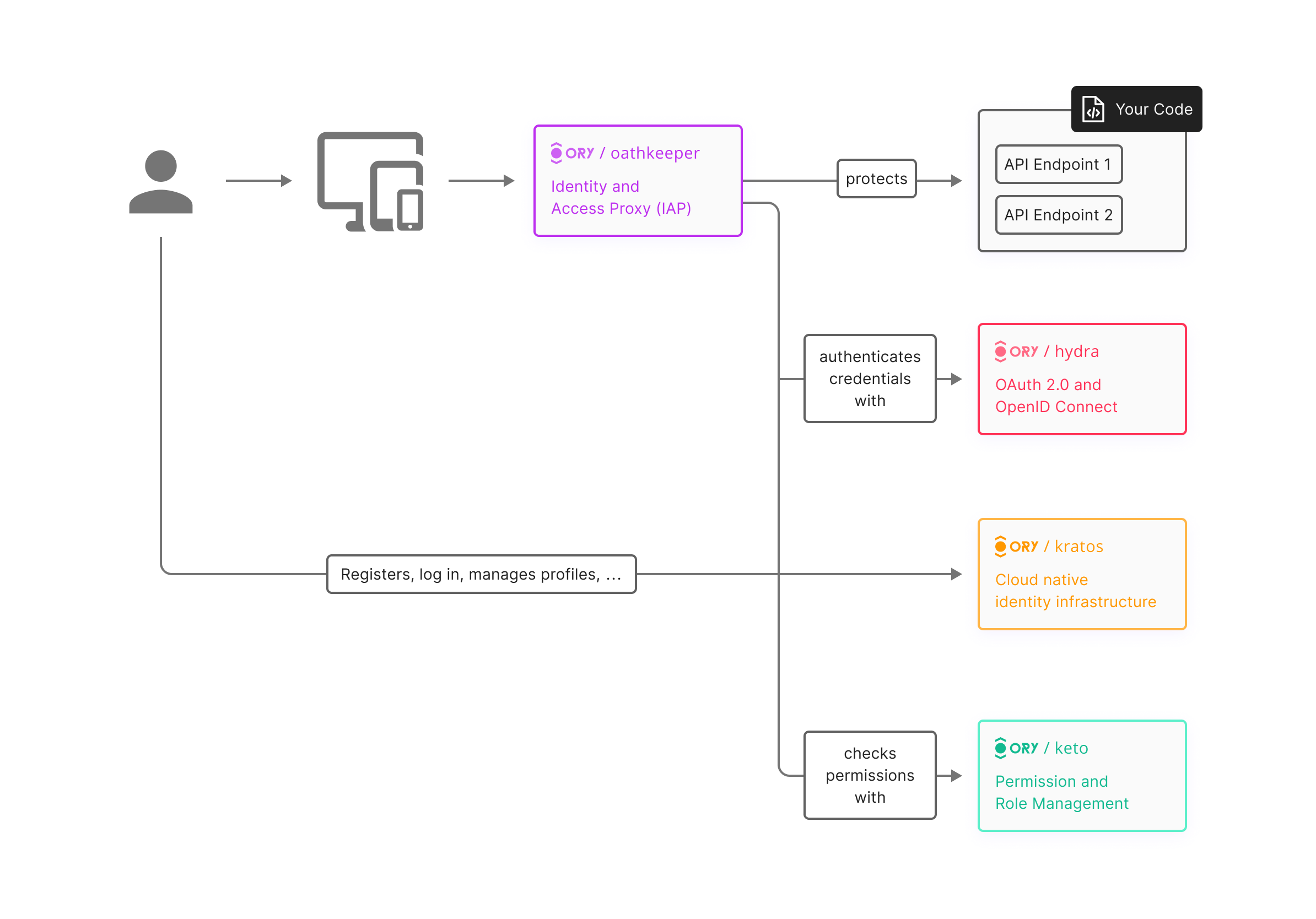
Getting Started with User Authentication and Account Creation using Ory Kratos
In the first post, we will dive into the world of user authentication with Ory Kratos. We'll set up secure user registration and authentication mechanisms easily thanks to Kratos.
Blog post Coming Soon
Enhancing API Security with Ory Oathkeeper
Our focus will shift to API security - a cornerstone of modern application architecture. Ory Oathkeeper takes the stage and I'll guide you through the implementation of robust security measures to ensure that your API is not vulnerable.
Blog post Coming Soon
Implementing a Permission System using Ory Keto
With Ory Keto and Zanzibar as our guide, we'll master the art of building a global authorization system that strikes the perfect balance between security and usability. Through in-depth tutorials and strategic insights, we'll empower you to architect an authorization framework that meets the organization's needs.
Blog post Coming Soon
Enabling Third-Party Access via Ory Hydra
Our final week unveils the power of enabling third-party access with Ory Hydra. By harnessing the capabilities of OAuth2 and OpenID Connect, I'll guide you through the intricacies of securely authorizing external consumers to access your APIs.
Blog post Coming Soon
As we embark on this journey together, our commitment to delivering authoritative and trustworthy content remains unwavering. We'll source our insights from official Ory documentation, industry best practices, and hands-on experience, ensuring that you receive the most accurate and up-to-date information.


